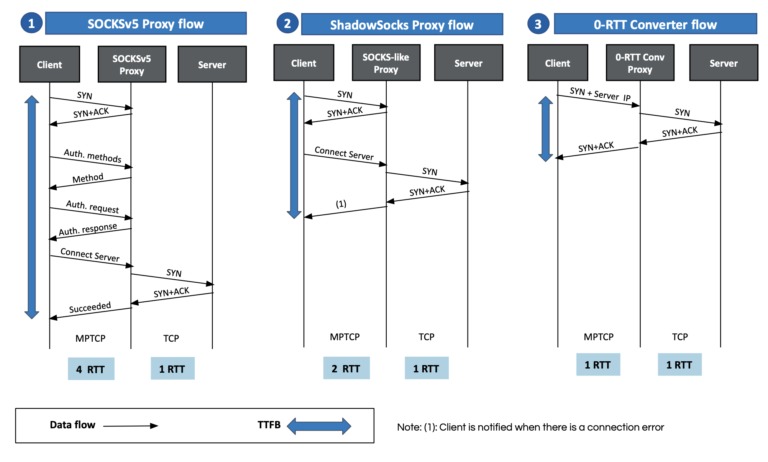
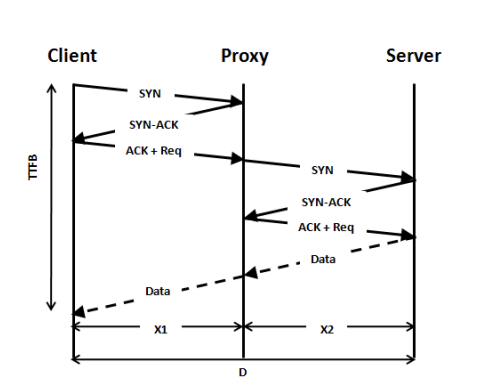
SYN-ACK-ACK proxy flood process. To initiate this attack on Juniper... | Download Scientific Diagram

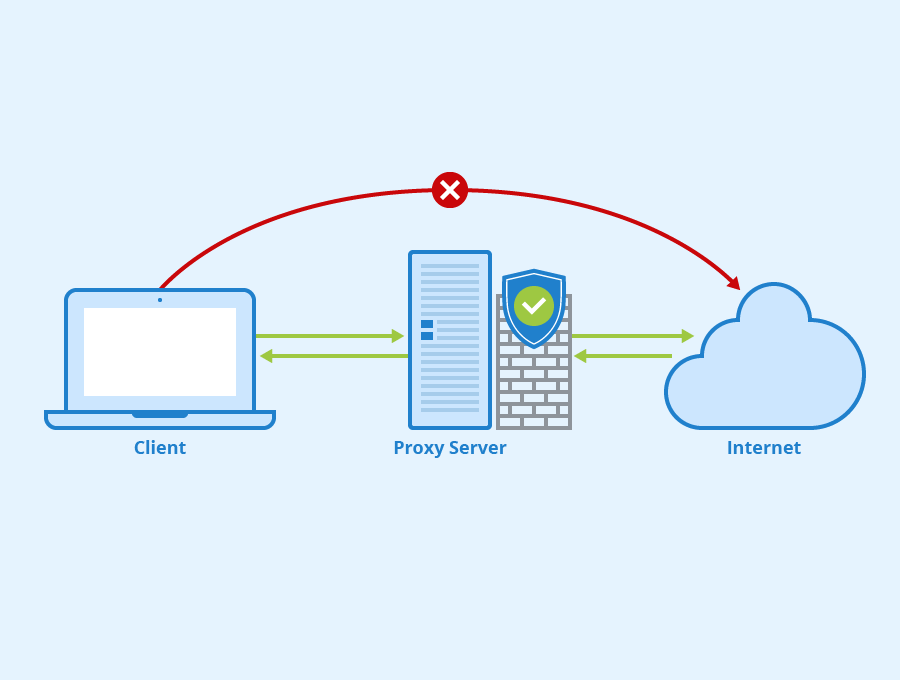
Architecture of SYN flood mitigation mechanism when used in Linux or as... | Download Scientific Diagram
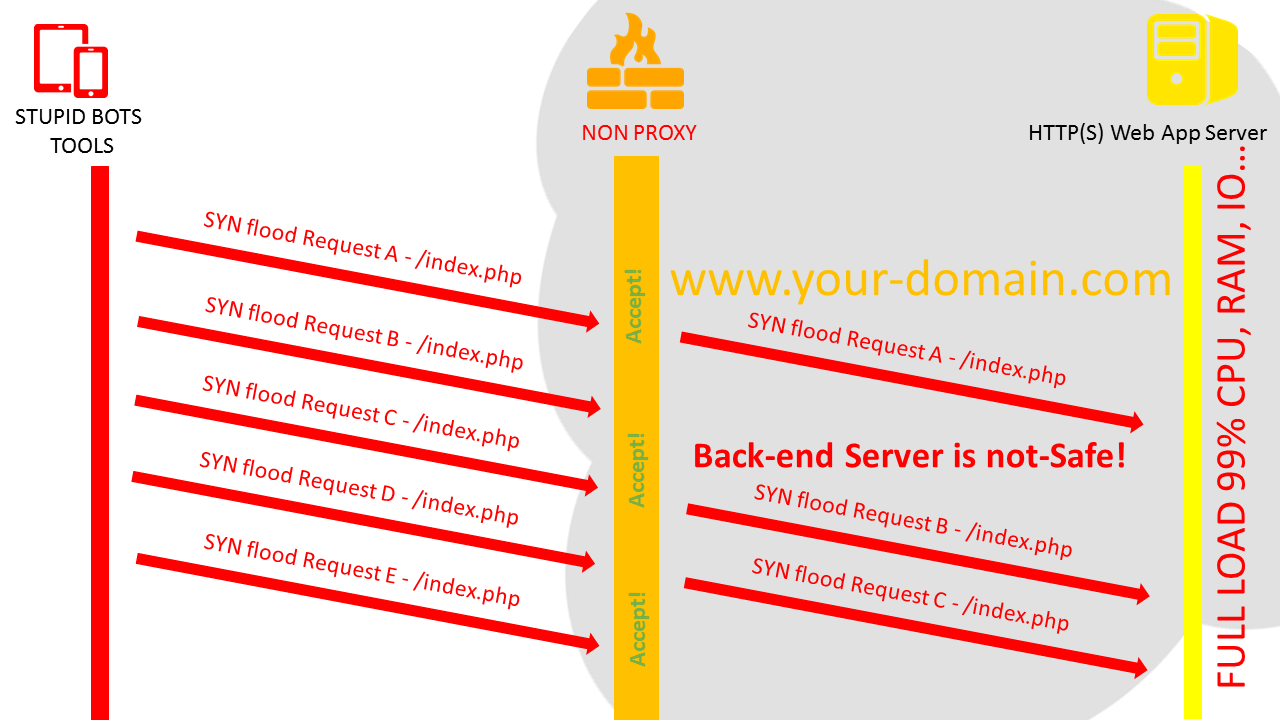
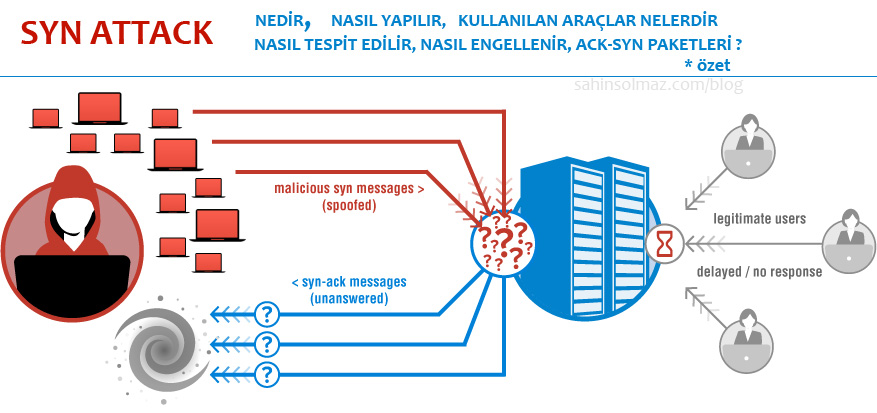
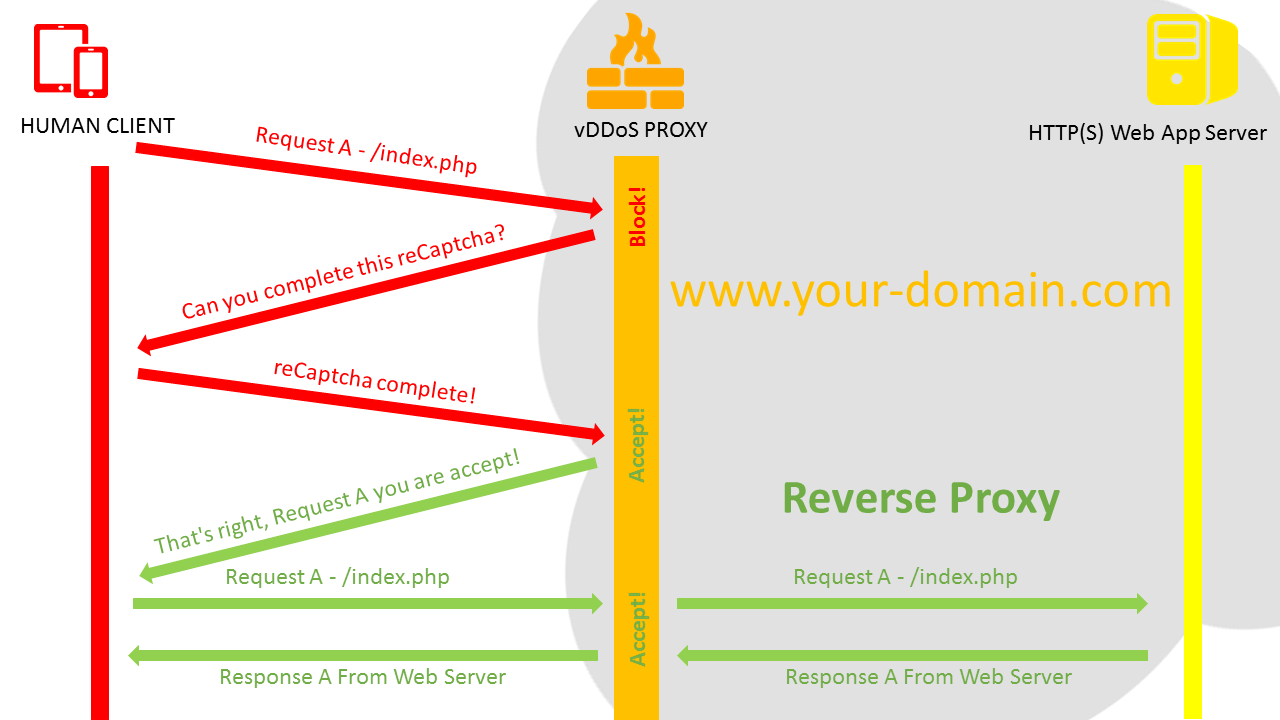
Syn Flood Nedir? Nasıl Önlenir? - Haber, Teknoloji, Yazılım ve Programlama ile ilgili makale ve içerikler

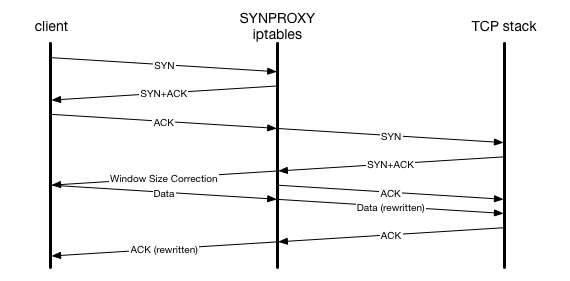
![Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram](https://www.researchgate.net/profile/Miroslav-Dulik/publication/336872866/figure/fig2/AS:956296866066433@1605010348044/Mechanism-of-SYN-cookies-4_Q320.jpg)










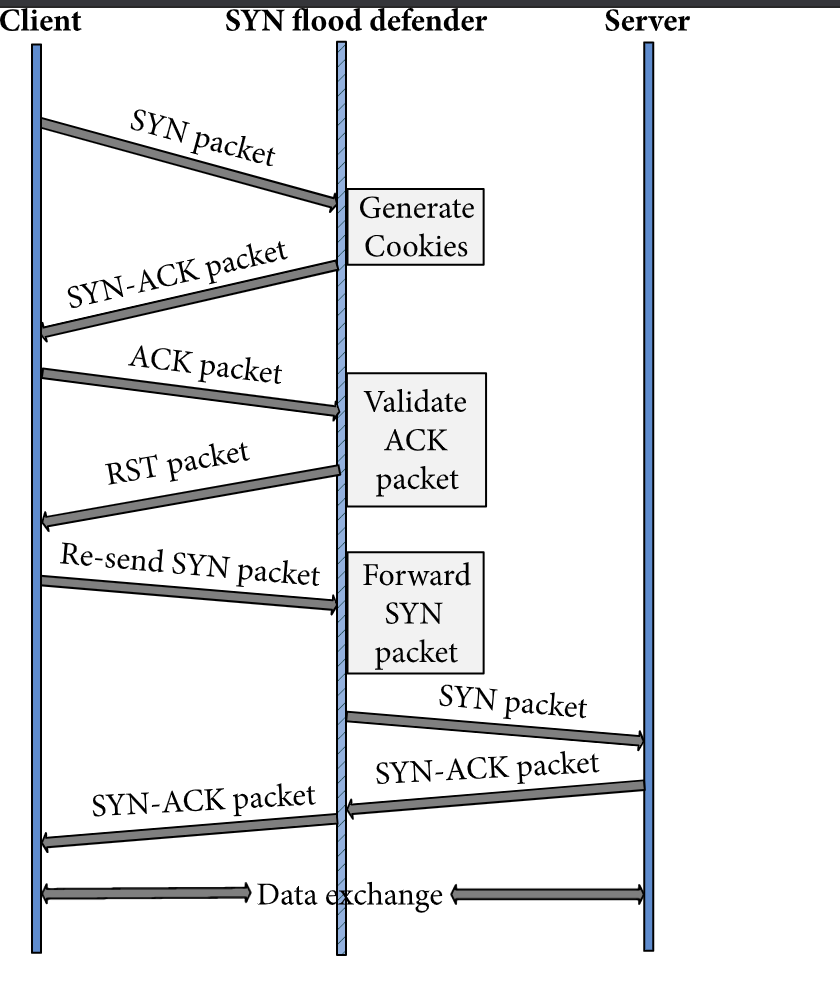



![Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram](https://www.researchgate.net/profile/Miroslav-Dulik/publication/336872866/figure/fig3/AS:956296866050053@1605010348138/Protection-against-SYN-flooding-using-SYN-Proxy-7_Q320.jpg)
![Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram Protection against SYN flooding using SYN Proxy [7] | Download Scientific Diagram](https://www.researchgate.net/publication/336872866/figure/fig3/AS:956296866050053@1605010348138/Protection-against-SYN-flooding-using-SYN-Proxy-7.jpg)